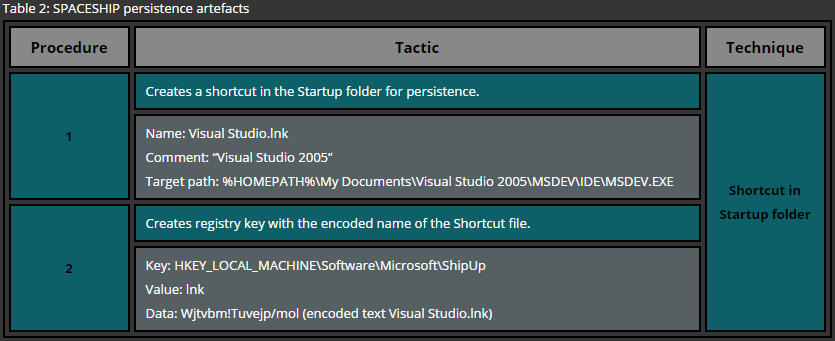
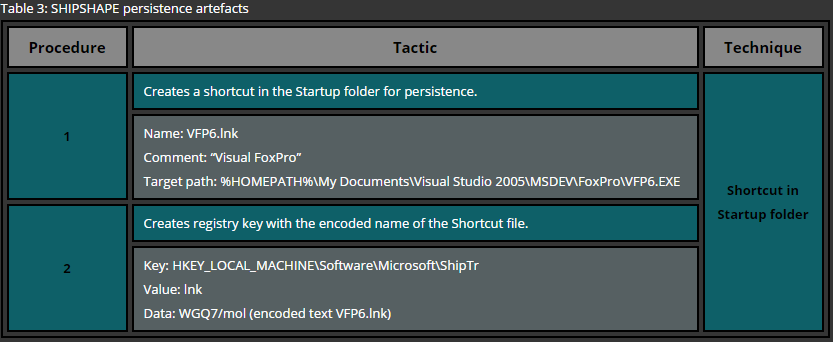
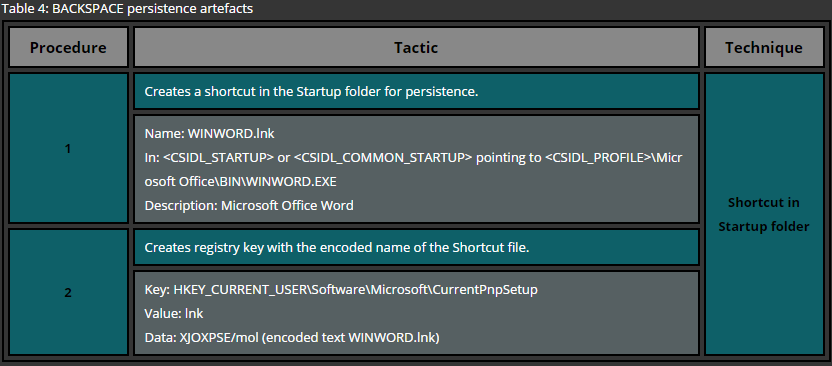
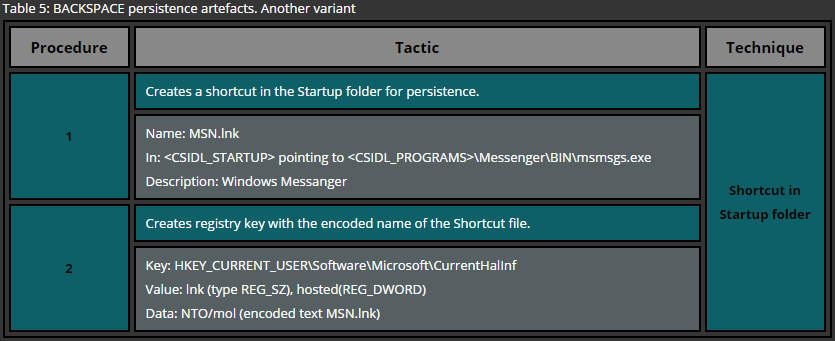
One of the most basic approaches for deploying persistence is the usage of startup folders. These folders are looked up by the Operating System during the startup and files, residing in such locations, are executed. Windows Operating system maintains two types of startup folder: user wide and system wide. While files located in the user’s startup folder is executed only for that particular user, files residing in the system wide startup folder is executed for every single user that logs onto the system.
A simple example of the persistence via startup folders for a specific user requires no administrative privileges and therefore is a common technique used across various attackers. In order to deploy persistence for all users via this technique administrative privileges are required as the system wide startup folder is protected by the operating system. This technique can be easily demonstrated by copying a file or a shortcut to one of the following folders.
Current User
Windows XP
C:\Documents and Settings\%USERNAME%\Start Menu\Programs\Startup
Windows Vista and later
C:\Users\%USERNAME%\Start Menu\Programs\Startup
All Users
Windows XP
C:\Documents and Settings\All Users\Start Menu\Programs\Startup
Windows Vista and later
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
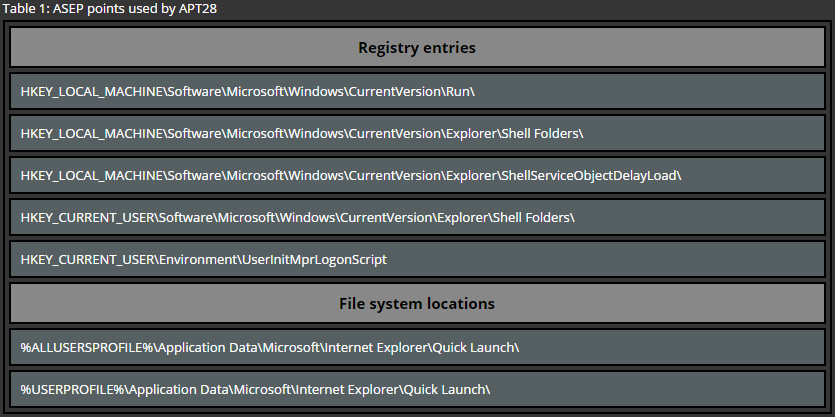
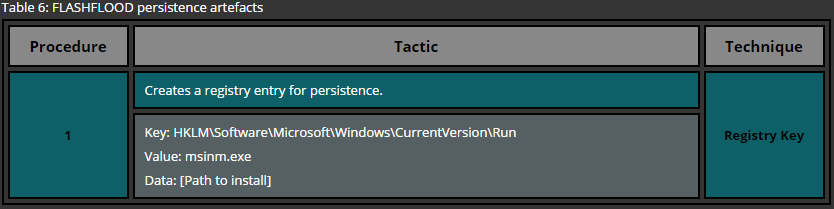
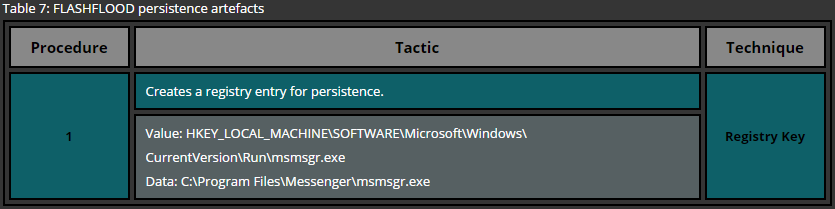
Another common technique used for persistence can be reproduced by creating registry keys under certain locations. Similar to the previous example, there are user wide and system wide registry location for program startup. Here again administrative privileges are required while deploying persistence for all users. The following list provides only the most common locations used for persistence via registry keys.
Current User
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
All Users
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
In order to implement a registry based persistence it is sufficient to execute one of the following commands.
Current User
REG ADD HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run /v calc /t REG_SZ /d C:\Windows\System32\calc.exe
All users
REG ADD HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run /v calc /t REG_SZ /d C:\Windows\System32\calc.exe
As a result of the above commands, the calculator application gets executed for the current user or for all users logging into the system.
While the provided examples are not advanced and can be easily discovered by an experienced computer user or system administrator it is often the case that attackers use more sophisticated approaches to deploy persistence. A few examples of such are service installation, DLL hijacking, rootkits, bootkits, etc. As an example of a more sophisticated way to maintain persistence is to upload a DLL to the victim’s computer and create a special registry key as shown below.
reg add "HKEY_CURRENT_USER\Software\Microsoft\Office test\Special\Perf" /t REG_SZ /d C:\Users\<username>\evil.dll
This registry key results in the malicious DLL being loaded every time when a Microsoft Office program, such as Word or Excel, is started [3]. It’s an uncommon technique, but yet quite effective as the user interaction triggers the malicious payload making it trickier for the Anti-Virus solutions to detect similar approaches.