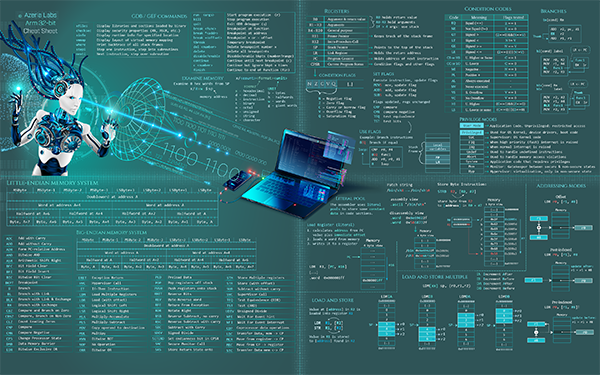
Sharing knowledge is an important part of our community. We all have knowledge worth sharing with others in our unique way and our preferred format. With tiny graphics and visualizations, the tutorials on this website are meant to ease the learning process of rather dry and complex topics.
Azeria Labs is split in two parts: the site you are currently on contains free tutorials and lab environments and aims to be a source of knowledge for people interested in topics around Arm reverse engineering and exploitation of IoT and mobile devices. This site will always contain free content and does not contain any ads. The business site of Azeria Labs is Azeria Labs Trainings, offering on-site private training for tech companies and at top-tier security conferences including Black Hat and Infiltrate.
Feedback is highly appreciated, and if you have any suggestions or constructive criticism, you can reach out via Twitter DM or email: feedback[@]azeria-labs.com.