The threat actor named as APT30 by FireEye is considered to be speaking Chinese. The language artifacts can be found by analyzing the metadata and the user interface of the malware used by APT30. The list of confirmed targets consists of companies and organizations in various fields operating in India, South Korea, Malaysia, Vietnam, Thailand, Saudi Arabia and United States. In addition to the confirmed countries, other countries in the region, like Singapore, Myanmar, Japan, etc., are also suspected to be targeted by the APT30 group [5].
From the publicly available information it is clear that APT30 is a motivated and determined threat group. A clear indication for this is the consistent long-term missions lasting for more than 10 years. Moreover, the tools used to carry out their attacks shows a strictly organized hierarchy and a consistent development indicating an involvement of a highly interested party which supports their attacks [5].
The APT30 group is linked to another threat actor named as Naikon. While Naikon seems to be also originating from within the China country, there is little evidence which correlates between these actors. Therefore, in order to analyze TTPs of this actor, the research focuses on indicators strictly associated with the group APT30.
Malware Components
The malware used by the APT30 group mainly targets Microsoft Windows operating systems. The core arsenal of this threat actor consists of two backdoors: BACKSPACE and NETEAGLE. These backdoors are usually delivered with attachments during a Spear-Phishing attack, either directly or via droppers. In addition to backdoors, SHIPSHAPE, SPACESHIP and FLASHFLOOD components are used in order to spread to air-gapped networks. The purpose of these components is to infiltrate systems disconnected from the network and steal valuable information [5]. The following table summarizes the first and last known compilation dates of the most common pieces of malware used by APT30.
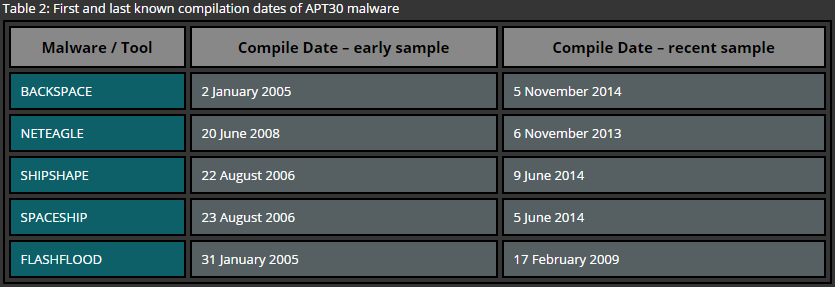
Table 2: First and last known compilation dates of APT30 malware
| Malware / Tool |
Compile Date – early sample |
Compile Date – recent sample |
| BACKSPACE |
2 January 2005 |
5 November 2014 |
| NETEAGLE |
20 June 2008 |
6 November 2013 |
| SHIPSHAPE |
22 August 2006 |
9 June 2014 |
| SPACESHIP |
23 August 2006 |
5 June 2014 |
| FLASHFLOOD |
31 January 2005 |
17 February 2009 |
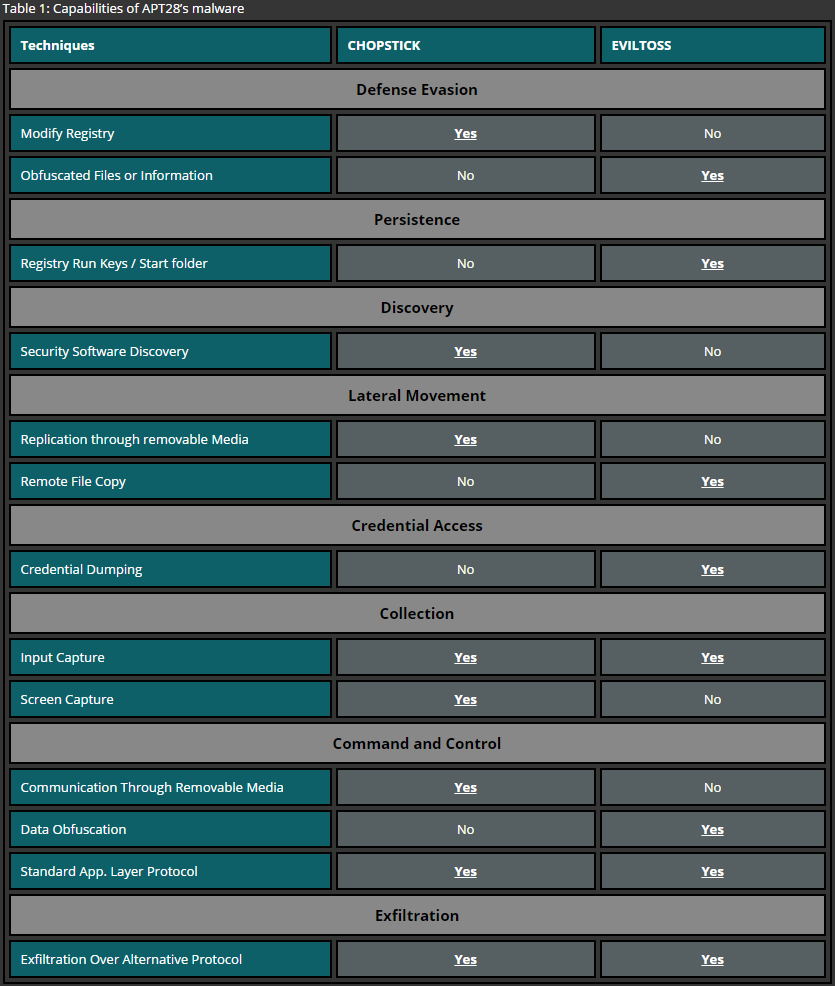
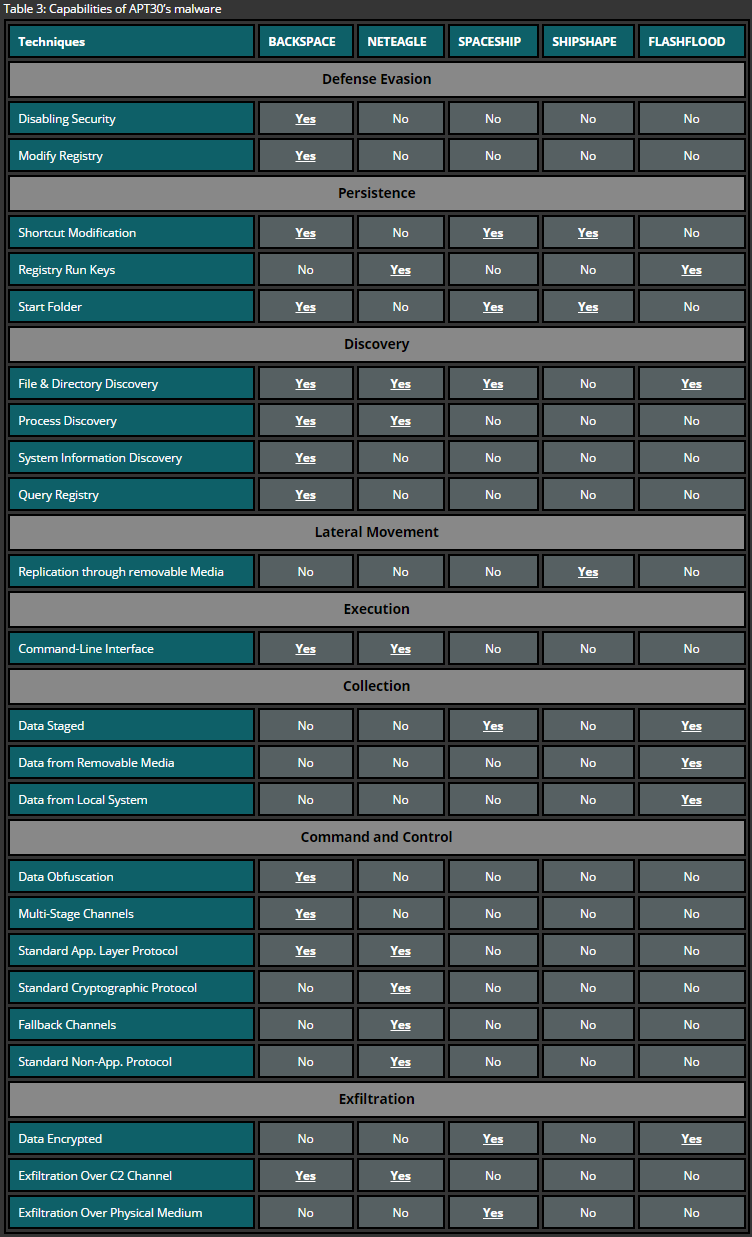
While BACKSPACE and NETEAGLE are different backdoors, they have multiple variations. Certain variants of both backdoors have modular design allowing attackers to create a customized version which suits specific environment of the target. While there are quite a lot of slight differences between BACKSPACE and NETEAGLE, the most notable difference is the usage of RC4 encryption in NETEAGLE’s variants compared to plain-text data transmission in BACKSPACE. This shows attacker’s attempt to use encryption as a technique of covering malicious activities from investigators. On the other hand, BACKSPACE included some notable features like ability to bypass host based firewalls in variations of ZR branch or a capability to reach out systems within the targets network having no direct internet access (variations in ZJ branch). Moreover, BACKSPACE variants implement a technique that allows to transmit metadata (such as file name, attributes, size, MAC time) to the threat actor who can then select files for uploading, resulting in less traffic transmitted over the target network and therefore reduces the chance of drawing attention. So, BACKSPACE and NETEAGLE seem to extend the capabilities of the APT30 group rather than replace each other.
SHIPSHAPE targets removable and fixed drives with a likely intent to spread malware to other systems. It targets drives with specific size and replaces files and folders on targeted drives by setting the hide option on the original files and planting SPACESHIP executables from specified paths on the computer infected with SHIPSHAPE. In order to be efficient, SHIPSHAPE is designed to name the executables under the names of the original files which were residing on the target drives. The purpose of the SPACESHIP component is to steal files based on a specified set of file extensions by copying these files to a removable drive inserted into the air-gapped systems infected with SPACESHIP. Identified samples of FLASHFLOOD have the capability to log or copy system information and contacts from the victim computer and implement similar capabilities to SPACESHIP, such as the same encoding process and the capability to search for and archive files based on pre-configured patterns. Unlike SPACESHIP, FLASHFLOOD scans inserted removable drives for interesting files in order to copy them from the removable drive to the computer infected with FLASHFLOOD.
Less documented malware components are MILKMAID and ORANGEADE droppers used by APT30 to install downloaders, such as CREAMSICLE, BACKBEND and GEMCUTTER. The purpose of those downloaders is to fetch and install BACKSPACE and NETEAGLE backdoors or to assure their persistence. The advantage of using droppers is small size of the component and lower likelihood of triggering Anti-Virus solutions which allows attackers to remain stealth.
Finally, traces of extensive versioning maintained by the group indicate that the malware used during their activities is developed continuously by adding new functions which allow to perform more sophisticated attacks. Moreover, actors try to make sure their targets are running the most recent version of the malware as the self-update functionality was observed across multiple samples of their backdoors. It is also important to note that an attempt to protect the backdoor controller software by implementing hardware checks indicates that this malicious software is intended to be used by a narrow group of users on a specific infrastructure.