The current approach used by the industry to deal with cyber-attacks is insufficient. This is mainly caused by the market which makes the customers, including enterprises, believe that an Anti-Virus solution combined with a Firewall and some additional automatic tools is sufficient in order protect from cyber threats. However, these cyber defenses are usually easily bypassed by a motivated and determined attacker. For example, most Anti-viruses are helpless against in-memory only malware or malware signed by a legitimate code signing certificate which might have been stolen by the attacker. Similarly, Firewalls and other network monitoring measures can be bypassed by camouflaging the malicious traffic in such a way that the traffic generated by the malware seems legitimate or inaccessible by the monitoring tools. It’s common to see malware successfully communicating over the HTTP protocol which mimics normal user’s behavior. In addition, the traffic can be encoded or encrypted making it difficult to analyze in an automatic approach. Finally, even the anti- Zero-Day countermeasures can be bypassed by attackers as some of those solutions are freely (i.e. EMET) or easily accessible for well-resourced attackers. Given enough motivation, determined attackers could install a defense mechanism that is needed to be bypassed and study it until a successful exploit is developed.
Another approach used within the industry to combat intrusion is to entirely rely on security software or appliances which use a pre-compiled and constantly updated list of Indicators of Compromise (IOCs). While this approach can be more comprehensive and could provide better results in detection of an intrusion compared to the classical AV/FW approach, it is still insufficient, because it is reactive by its nature. This is because IOCs are compiled after the analysis of certain infections and thus can only provide protection against known threats. Moreover, these IOCs can be accessible to any motivated threat actor and therefore be used to adjust its tools to successfully perform future campaigns. Therefore, relying on these static indicators as a mechanism to identify APTs will have low impact on a broader malicious operation that is carried out by a determined and sophisticated threat.
Once the correlation and the effort required for the attacker to bypass obstacles put by defenders is understood, the importance of fighting the threat actor’s TTPs rather than static IOCs becomes obvious. Additionally, the impact that the exposure will have on the attacker increases with every step going up the pyramid illustrated in Figure 1. Therefore, it is important to redesign the current approach and implement a behavior oriented detection and incident response methodology in order to stop attacks from occurring or making the recovery more efficient.
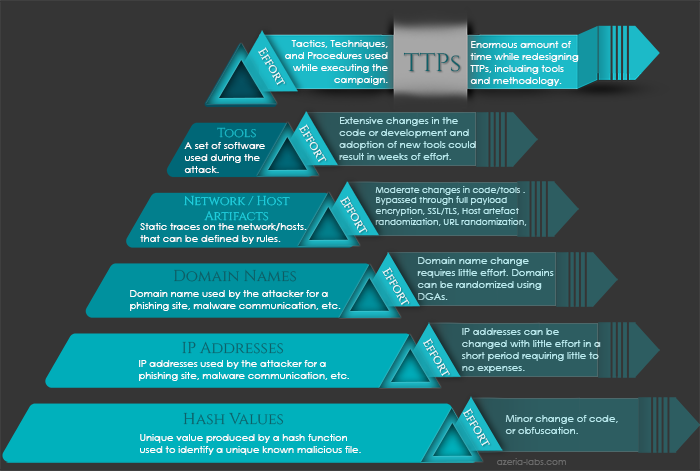
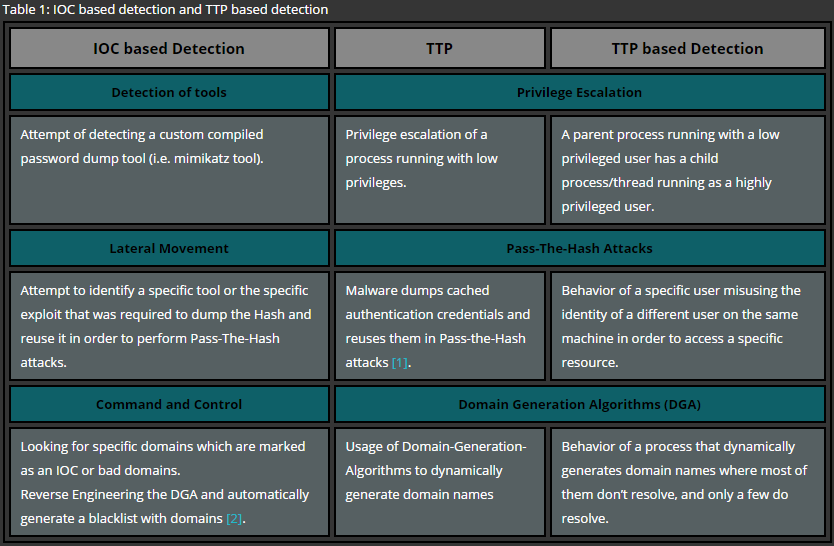
The following table illustrates the idea of enhancing current threat intelligence procedures by showing basic examples of the difference between an IOC based detection and a TTP based detection.
By combining classical approaches with a more dynamic and intensive behavioral analysis of Advanced Persistent Threats, a more comprehensive profile of threats can be created which allows to minimize the risk of being compromised. This means that instead of relying on automatic security solutions the defender needs to first understand the Tactics, Techniques, and Procedures of its enemy and then start planting obstacles which could prevent from a highly-motivated attacker, such as an APT. This could be achieved by constantly studying occurring attacks in the wild, analyzing their TTPs, building and training blue teams to understand the mindset of an Advanced Persistent Threat actor, engaging the blue team with a red team in order to keep up with sharp and decent skills for detecting intrusion attempts and implementing prevention mechanisms. While there is no silver bullet to cyber-attacks, causing a significant amount of pain for an adversary the defender can drastically reduce the likelihood of a successful breach. Therefore, it is important to fully understand the concept of TTPs as exposing TTP patterns will have the most impact on the adversary.
