February 10, 2020
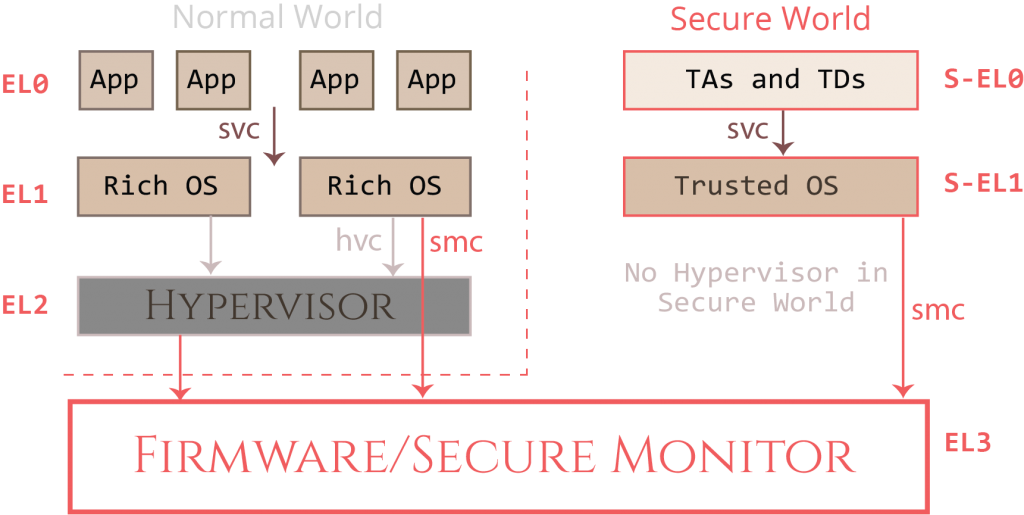
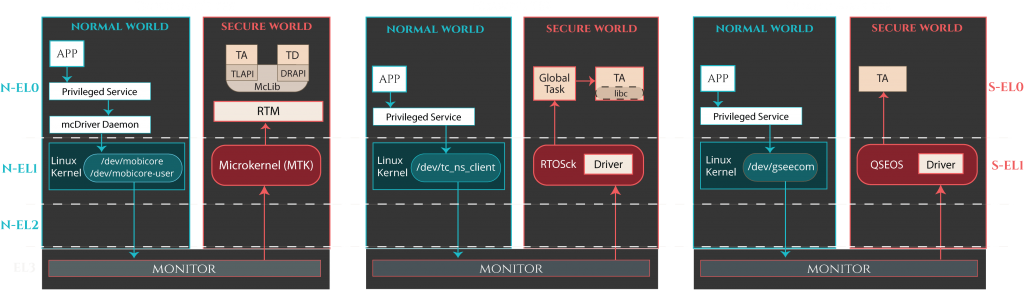
This post is the first part of a larger series and aims to ease the process of getting started with TrustZone security research. If you ever wondered how Trusted Execution Environments on modern Android phones work and want to learn about their attack surface, you will find enough information in this series to get you started. In this introduction post, you will learn what the TrustZone technology is and what Trusted Execution Environments (TEE) are for. You can use this post as a reference for TrustZone and TEE concepts you don’t understand or remember when reading the follow-up posts.
The next parts of this series will cover topics like
- The Kinibi TEE implementation used in Samsung devices
- The Qualcomm TEE implementation
- Reverse Engineering TEE components
- The TEE attack surface
- TEE Design flaws that have been published in recent years
- How input handling vulnerabilities in certain TEE components can lead to privilege escalation
- Exploit mitigations on current TEE implementations