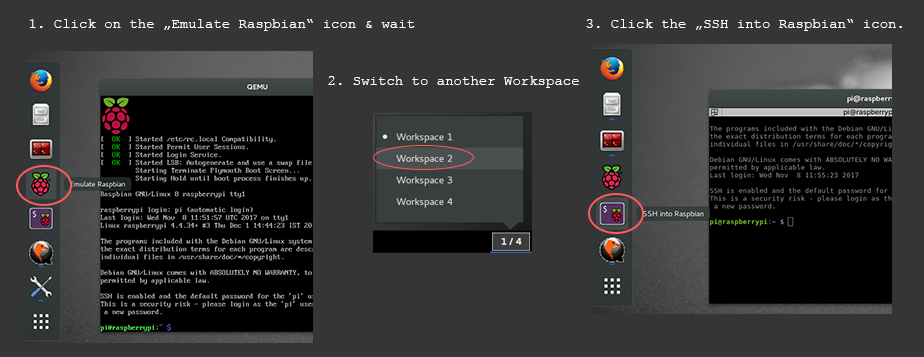
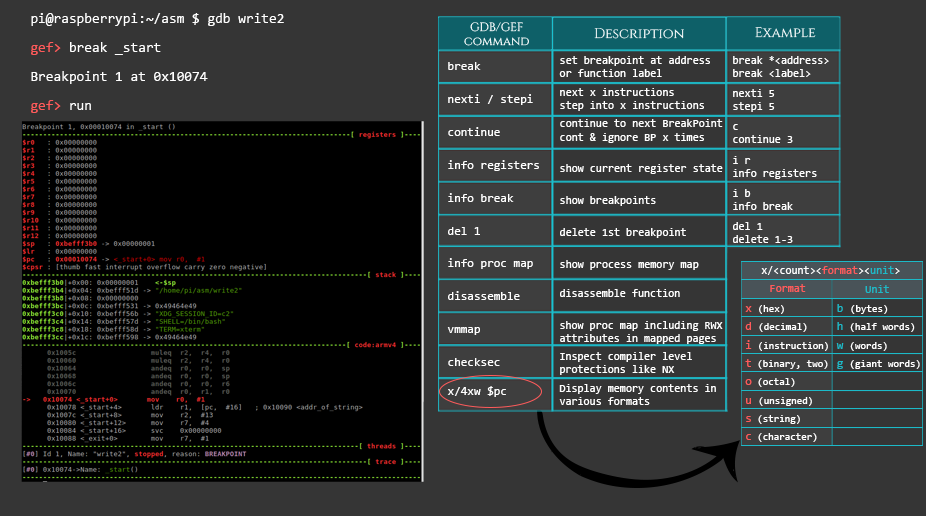
Run your first challenge in GDB and set a breakpoint at the main function:
pi@raspberrypi:~/ARM-challenges $ gdb stack0
gef> b main
Breakpoint 1 at 0x1044c
gef> run
Your binary reached the first breakploit. This is what you should see:
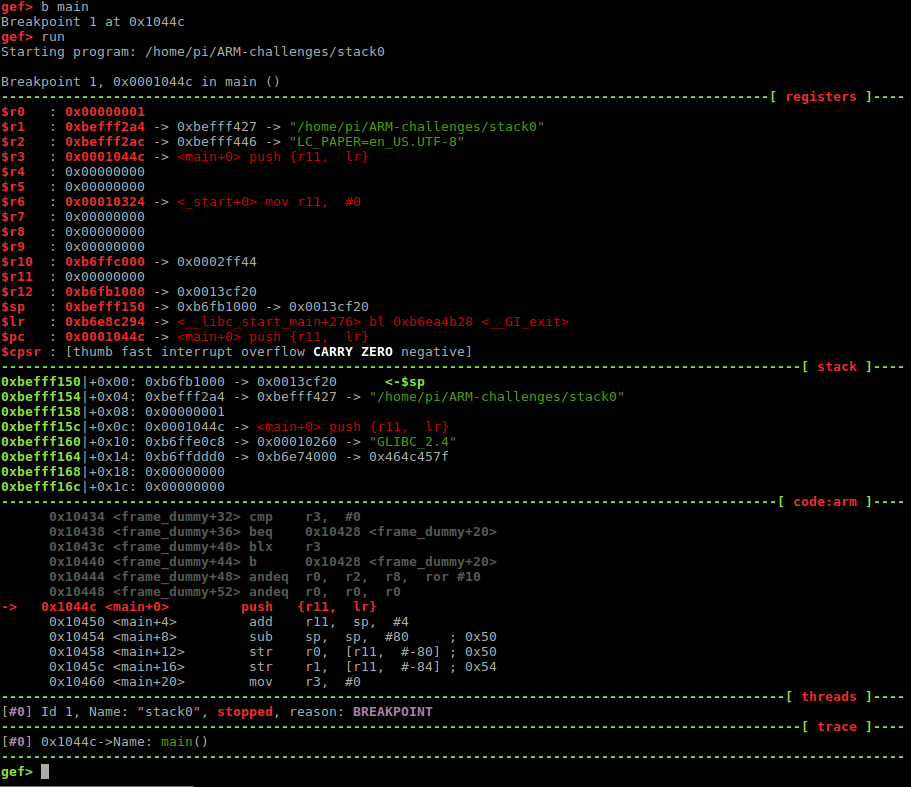
Now, let’s look at the main function with “disassemble main”.
gef> disassemble main
Dump of assembler code for function main:
=> 0x0001044c <+0>: push {r11, lr}
0x00010450 <+4>: add r11, sp, #4
0x00010454 <+8>: sub sp, sp, #80 ; 0x50
0x00010458 <+12>: str r0, [r11, #-80] ; 0x50
0x0001045c <+16>: str r1, [r11, #-84] ; 0x54
0x00010460 <+20>: mov r3, #0
0x00010464 <+24>: str r3, [r11, #-8]
0x00010468 <+28>: sub r3, r11, #72 ; 0x48
0x0001046c <+32>: mov r0, r3
0x00010470 <+36>: bl 0x102e8
0x00010474 <+40>: ldr r3, [r11, #-8]
0x00010478 <+44>: cmp r3, #0
0x0001047c <+48>: beq 0x1048c <main+64>
0x00010480 <+52>: ldr r0, [pc, #24] ; 0x104a0 <main+84>
0x00010484 <+56>: bl 0x102f4
0x00010488 <+60>: b 0x10494 <main+72>
0x0001048c <+64>: ldr r0, [pc, #16] ; 0x104a4 <main+88>
0x00010490 <+68>: bl 0x102f4
0x00010494 <+72>: mov r0, r3
0x00010498 <+76>: sub sp, r11, #4
0x0001049c <+80>: pop {r11, pc}
0x000104a0 <+84>: andeq r0, r1, r12, lsl r5
0x000104a4 <+88>: andeq r0, r1, r8, asr #10
End of assembler dump.
gef>
Step through the instructions and watch how the registers and the stack values change. For that, you can use the commands “nexti” or “stepi”.
If you continue the program with “continue” or “c”, it will expect some input from you:
gef> c
Continuing.
Try screaming at it a little (with AAAAAAAAA’s) and see what happens:
gef> c
Continuing.
AAAAAAAAAAAAAAA
Try again?
[Inferior 1 (process 913) exited normally]
gef>
Oh, that was not enough screaming it seems. Try again and scream a little more. But first, run the binary again:
gef> run
Starting program: /home/pi/ARM-challenges/stack0
Breakpoint 1, 0x0001044c in main ()
[...]
gef> c
Continuing.
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
you have changed the 'modified' variable
Program received signal SIGSEGV, Segmentation fault.
0x41414140 in ?? ()
Yaaay! You got it! You successfully changed the ‘modified’ variable and caused the program to crash.